Introduction to Proactive Opsec Planning
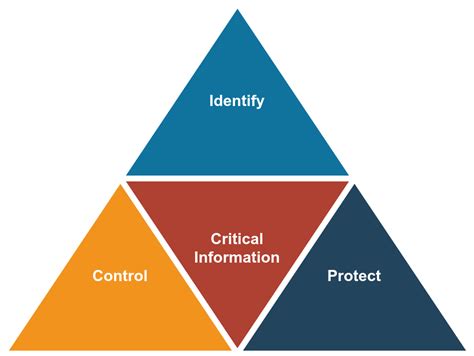
Operational Security (Opsec) is a critical practice that focuses on protecting sensitive information and ensuring the security of operations. It involves a proactive approach to identify and mitigate potential risks and threats. In today’s digital age, where data breaches and cyber attacks are prevalent, implementing effective Opsec measures is essential for individuals, businesses, and organizations. This comprehensive guide will take you through the process of proactive Opsec planning, covering various aspects to enhance your security posture.
Understanding the Importance of Opsec
Opsec is more than just a security protocol; it is a mindset and a culture that promotes a secure environment. By adopting a proactive Opsec approach, you can:
- Protect Sensitive Information: Opsec planning helps identify and safeguard critical data, preventing unauthorized access and potential misuse.
- Mitigate Risks: Through thorough risk assessment and management, Opsec reduces the likelihood of successful attacks or data breaches.
- Maintain Operational Integrity: By securing operations, Opsec ensures the continuity and reliability of your business or organization.
- Build Trust: Effective Opsec practices enhance the trust of your customers, partners, and stakeholders, fostering long-term relationships.
Assessing Your Current Opsec Posture

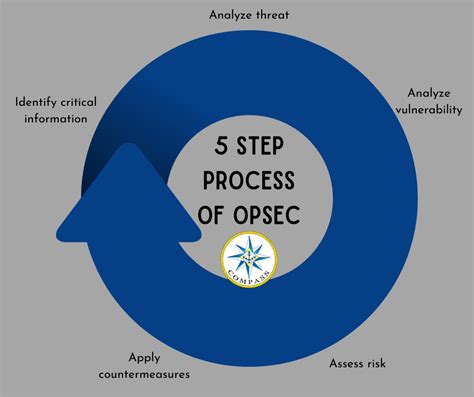
Before implementing proactive Opsec measures, it is crucial to evaluate your current security posture. This assessment will help identify areas of improvement and prioritize your Opsec planning. Here’s how to get started:
Step 1: Identify Sensitive Assets

- Data Classification: Classify your data based on sensitivity levels. Identify personally identifiable information (PII), financial records, intellectual property, and other critical assets.
- Asset Inventory: Create a comprehensive inventory of all your digital and physical assets. Include servers, networks, devices, and even third-party services you rely on.
Step 2: Conduct a Risk Assessment

- Threat Identification: Research and identify potential threats relevant to your industry and assets. Consider cyber attacks, data breaches, physical security breaches, and human errors.
- Vulnerability Analysis: Assess the vulnerabilities associated with your assets. Look for weak points in your network, systems, and processes that could be exploited.
- Impact Analysis: Evaluate the potential impact of a security breach on your operations, reputation, and financial stability.
Step 3: Analyze Current Security Measures

- Review Existing Policies: Evaluate your current security policies and procedures. Identify gaps and areas where improvements can be made.
- Audit Security Controls: Assess the effectiveness of your security controls, such as firewalls, encryption, access controls, and incident response plans.
- Employee Training: Evaluate the security awareness and training programs for your staff. Ensure they understand their role in maintaining Opsec.
Developing a Proactive Opsec Plan

Based on your assessment, it’s time to develop a comprehensive Opsec plan. This plan should be tailored to your specific needs and should address the identified risks and vulnerabilities. Here’s a step-by-step guide:
Step 1: Define Opsec Objectives

- Clear Goals: Set specific and measurable Opsec objectives. Define what you aim to achieve with your Opsec plan, such as reducing the risk of data breaches or improving incident response times.
- Prioritize Objectives: Prioritize your objectives based on the criticality of the assets and the potential impact of a breach.
Step 2: Implement Security Controls
- Network Security: Enhance your network security by implementing firewalls, intrusion detection systems, and secure network protocols.
- Data Protection: Employ encryption techniques to protect sensitive data both at rest and in transit.
- Access Controls: Implement strong access controls, including multi-factor authentication and role-based access, to restrict unauthorized access.
- Endpoint Security: Ensure all devices, including laptops and mobile phones, have adequate security measures and are regularly updated.
Step 3: Establish Security Policies and Procedures

- Documented Policies: Create comprehensive security policies that cover various aspects, such as password management, remote access, and data handling.
- User Awareness: Develop training programs to educate your staff about security best practices and their responsibilities.
- Incident Response Plan: Establish a detailed incident response plan that outlines the steps to be taken in the event of a security breach or incident.
Step 4: Continuous Monitoring and Improvement

- Regular Audits: Conduct periodic security audits to identify any new vulnerabilities or weaknesses.
- Threat Intelligence: Stay updated with the latest threat intelligence and adapt your Opsec plan accordingly.
- Feedback Loop: Encourage feedback from your team and stakeholders to continuously improve your Opsec practices.
Advanced Opsec Strategies

To further enhance your Opsec planning, consider implementing these advanced strategies:
1. Red Teaming and Blue Teaming
- Red Team: Employ a dedicated team to simulate real-world attacks and identify vulnerabilities in your systems and processes.
- Blue Team: Build a team responsible for defending against the red team’s attacks and improving your security posture.
2. Supply Chain Security

- Vendor Assessment: Conduct thorough assessments of your third-party vendors and suppliers to ensure they meet your security standards.
- Contractual Agreements: Include security clauses in your contracts to hold vendors accountable for any security breaches or incidents.
3. Insider Threat Management
- Employee Screening: Implement rigorous background checks and screening processes for new hires to minimize the risk of insider threats.
- Access Reviews: Regularly review and revoke access privileges for employees who no longer require them.
Implementing Opsec in Your Organization

When implementing Opsec measures, it’s essential to involve key stakeholders and ensure buy-in from all levels of your organization:
- Executive Support: Gain support from the top management to allocate resources and prioritize Opsec initiatives.
- Cross-Functional Collaboration: Involve departments such as IT, HR, legal, and operations in the Opsec planning process.
- Communication and Training: Communicate the importance of Opsec to all employees and provide regular training sessions to reinforce security practices.
Measuring Opsec Effectiveness

To evaluate the success of your Opsec plan, consider the following metrics:
- Security Incident Reduction: Track the number of security incidents and compare them over time to measure the effectiveness of your Opsec measures.
- User Awareness: Assess the security awareness of your employees through regular surveys and feedback.
- Compliance and Audits: Ensure compliance with relevant security standards and regulations, and successfully pass security audits.
Conclusion

Proactive Opsec planning is a continuous process that requires dedication and a security-first mindset. By following the steps outlined in this guide, you can create a robust Opsec plan tailored to your organization’s needs. Remember, effective Opsec is not a one-time effort but an ongoing commitment to protect your sensitive information and maintain a secure operational environment. Stay vigilant, stay informed, and adapt your Opsec strategies as new threats and technologies emerge.
FAQ

What is the difference between Opsec and InfoSec?
+
Operational Security (Opsec) focuses on protecting sensitive information and securing operations, while Information Security (InfoSec) primarily deals with safeguarding data and systems from unauthorized access, use, disclosure, disruption, modification, or destruction.
How often should I update my Opsec plan?
+
It is recommended to review and update your Opsec plan at least annually or whenever there are significant changes in your organization, such as new technologies, personnel, or security threats.
What are some common Opsec mistakes to avoid?
+
Common Opsec mistakes include relying solely on technical solutions without considering human factors, neglecting regular security training and awareness programs, and failing to conduct thorough risk assessments.
How can I ensure employee buy-in for Opsec initiatives?
+
To ensure employee buy-in, communicate the importance of Opsec and its impact on the organization’s success. Provide clear guidelines, offer regular training, and recognize employees who demonstrate strong Opsec practices.
What are some best practices for remote work Opsec?
+
For remote work Opsec, ensure employees use secure connections, have up-to-date antivirus software, and follow strong password practices. Provide guidance on secure data storage and sharing, and regularly remind employees about the importance of maintaining a secure work environment.